Requirements
SSL certificates are required for the Sureview App and Device Tier servers to encrypt the data between the clients and the servers as per the Minimum Requirements (note: you will need 2 certificates if your App and Device Tier servers are separate in a scaled deployment).
Provider Options
SSL Certificates can be created for the hostnames of your App and Device tier servers either by...
- Your IT team
- An external provider such as GoDaddy if your IT team does not provide this service (refer to the provider's documentation for this, and SureView staff can also provide advice on the process)
IMPORTANT: the provided certificate must be valid as per the requirements in the "Checking Certificate Validity" section below
Guidance: Managing Computer Certificates
After you have obtained a certificate it must be added to the Sureview servers.
Computer certificates can be managed either via:
- PowerShell: this can always be used whether you have access to the Windows GUI or not and can also be scripted so we will use it here.
- The "Certificates" snap-in for the Microsoft Management Console: this is only available if you have access to the Windows GUI and cannot be scripted. Follow the Microsoft instructions to use this.
Listing computer certificates
To get the list of currently installed computer certificates with their hash (thumbprint) run this PowerShell command:
Get-ChildItem -Path cert:\LocalMachine\My -Recurse
Importing a certificate file
To import a computer certificate from a PFX file run this PowerShell command, changing the filename marked in bold and providing the password:
$certFile = "YourPFXFile.pfx"
$certPass = Read-Host -AsSecureString -Prompt "Enter password for PFX file";
Import-PfxCertificate -FilePath $certFile -Password $certPass -CertStoreLocation cert:\LocalMachine\My -Exportable
Important: after importing a certificate you must make sure you check that it is valid before proceeding any further (see the "Checking Certificate Validity" guidance below). An invalid certificate may cause some or all parts of the software to experience issues and must be corrected before proceeding.
Guidance: Checking Certificate Validity
The certificate must be valid before proceeding any further otherwise some or all parts of the SureView UI may not work.
Requirements
The requirements for a valid certificate are:
- It must have a "Valid From" date that is in the past and a "Valid To" date that is in the future.
- It must be trusted by all clients being used to access the server, which means:
- It must have a Subject Alternative Name that covers the hostnames being used by clients to access the server (i.e. if clients are using "sureview.yourdomain.com" to access the server then the certificate must either cover "sureview.yourdomain.com" or "*.mydomain.com")
- It must be signed by a Certification Authority that clients trust. Self-signed certificates cannot be used in production unless the IT team is able to take the additional steps needed to make all clients and servers able to trust it
- The server must have a certificate path that allows the certificate to be verified. The simplest way to achieve this is to tick the "Include all certificates in the certification path" option when exporting the PFX file, otherwise you will need to import all the intermediate certificates to the server too.
- The server must have the private key for the certificate. The simplest way to achieve this is to tick the "Export the private key" option when exporting the PFX file.
Checking
To check these details, use MMC to view the properties of the computer certificate (run "mmc" then go to File->Add/Remove Snap-In, then choose the "Certificates" snap-in, and select "Computer account"), it must have the following:
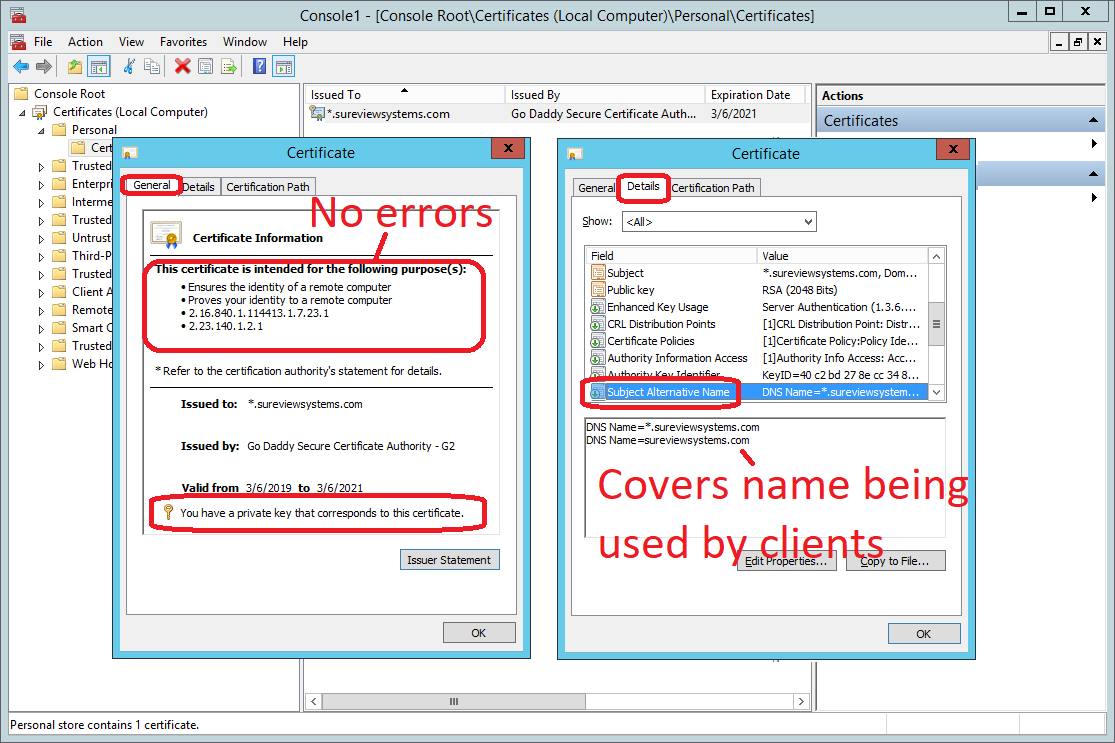
- There must be no errors in the "Certificate Information" box at the top of the "General" tab. Common errors include:
- "The certificate has expired or is not yet valid" - either the certificate's end date has been passed or the certificate's start date is in the future
- "Windows does not have enough information to verify this certificate" - the certificate path is not complete, likely meaning you are missing the intermediate certificates (see the Requirements above for how include this with the PFX)
- It must say "You have a private key that corresponds to this certificate" at the bottom of the "General" tab (see the Requirements above for how to include this with the PFX)
- The "Subject Alternative Name" in the "Details" tab must cover the hostname being used by clients to access the server (for scaled deployments this includes the URL used to access the Web UI for App Tier servers, and the endpoints used for Device Server and Audit on Device Tier servers).
Guidance: Managing Certificate Port Bindings
After importing a certificate it must be bound to ports in order for it to be used.
Listing port bindings
Run the following command to list all port bindings
netsh http show sslcert
Binding a certificate to a port
Run the following command to bind a certificate to a port, providing the items marked in bold of:
- The port number
- The Certificate Hash found using the steps in "Listing computer certificates" above.
- The appID `{5bfe1d7c-ffa2-4c91-b070-a279adaebff8`}
(this exact ID should be use for any bindings on any SureView servers)
NOTE: if using Command Prompt rather than PowerShell then remove the ` backticks.
netsh http add sslcert ipport=0.0.0.0:YourPortNumber certhash=YourCertHash appid=`{5bfe1d7c-ffa2-4c91-b070-a279adaebff8`}
Deleting a certificate binding
Run the following command to remove the binding of a certificate to a port, providing the items marked in bold of:
- The port number
netsh http delete sslcert ipport=0.0.0.0:YourPortNumber
Comments
0 comments
Please sign in to leave a comment.